We’ve all come across suspicious links—whether in shady emails, social media posts, WhatsApp messages, or forums. The best course of action? Steer clear.
But if you’re like me and frequently search the web—especially for technical solutions, scripts, and programs—you might find yourself staring at a link posted by a stranger on a forum or blog. It could lead to the answer you need… or straight into a disaster.
Or maybe you’ve received an email from a legitimate sender, but you’re not 100% sure about the link inside. Or you are a security professional and want to test malicious links for testing and research. What do you do in moments like these?
Well, I’ve found the perfect solution! The word “perfect” is not a word I use often – because nothing is perfect in real life. But in this case, this is as close to you can get to perfection. Not only for suspicious links, but you can also use this to browse anything you want on the Internet with zero worries.
Enough preamble. Let’s get to it! This is basically an extended use of Kasm Workspaces. I posted a detailed guide on what it is and how to set it up from scratch. Please go through it using this link here. Once your Kasm Workspace Server is up and running, you can continue this guide.
We’re going to use Firefox Workspace for this. First, we’ll understand the mechanics, and then we’ll set it up in a more convenient, ready-to-go way.
Why is this so secure
Let’s see what makes this method of access so secure. First, log into Kasm Workspaces and launch a Firefox Workspace.
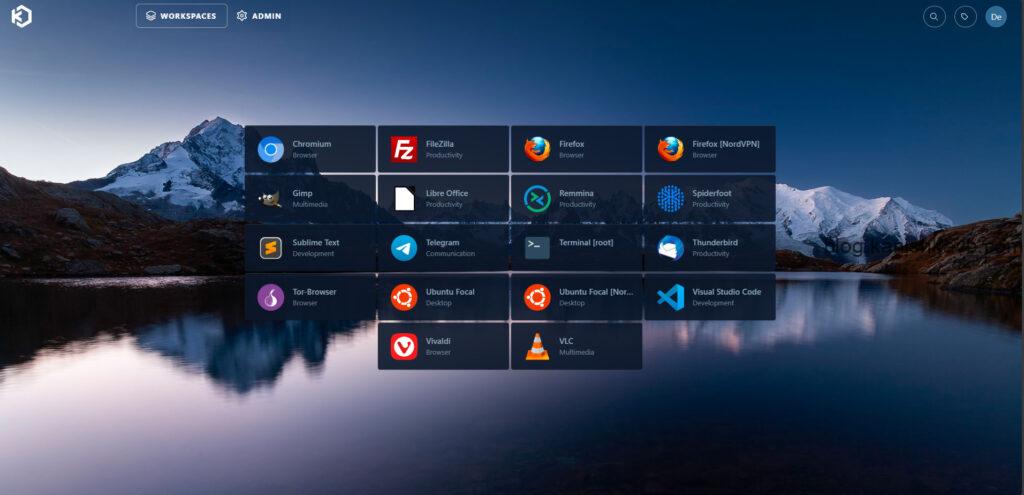

As I explained in my first post about Kasm, what we have here is essentially a Docker container running Firefox on Ubuntu. This container runs on a remote Kasm server (Kasm host), and its screen is streamed to our local machine’s browser.
When we visit a web page inside the Firefox Workspace, it essentially acts as a proxy. The container within the Kasm host accesses the web page, while we simply stream and control the browser—just like a remote login.
Let’s assume the web page we visit is malicious. It does not affect our host machine because,
- Any malicious code that executes affects only the Firefox browser inside the Workspace—not your local browser.
- Any malicious files you download are saved to the Workspace—not your local machine.
- All changes remain contained within the Workspace.
- The Workspace is an ephemeral Docker container. Simply destroy the session and start a new one, and any ‘damage’ is wiped clean, with all data erased.
Moreover, I would highly recommend you to use a dedicated cloud instance (in my case Oracle Cloud Compute Instance) for this. Then, even if something ‘breaks out’ of the Docker container (highly unlikely) there is no damage to be done since the Kasm host is just a VM on cloud. Even if something breaks, you can terminate the compute instance and create a new one. This practice is a must if you are ‘playing outside the lines’ by making customizations to the containers such as granting root access (not best practice) to the Workspace, mapping persistence folders from Kasm host etc.
Kasm host (server-side) setup
Let’s get to it. I don’t think I need to explain how to open a suspicious link the usual way—it’s obvious. Just copy the link, paste it into the Firefox browser inside the Firefox Workspace, visit the link, and do what you need to do.
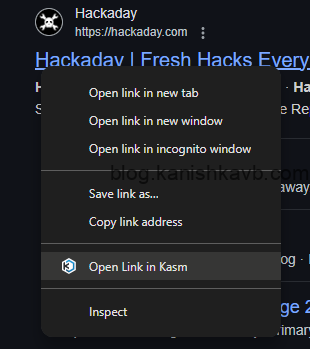
But there’s an easier, seamless way to handle this without manually logging into Kasm and copying links. We can integrate the Workspace with our local browser using a browser extension. This adds a Open Link in Kasm option when you right-click any link.
With this setup, Kasm will automatically spin up a Firefox Workspace and open the link inside it—all in the background. No manual steps, just a simple right-click and select the Kasm option. Let’s set this up.
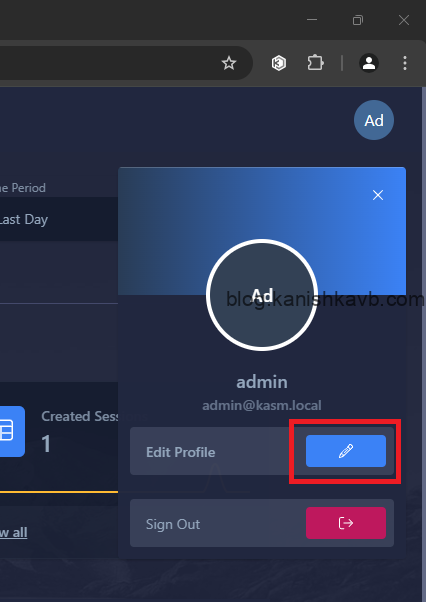
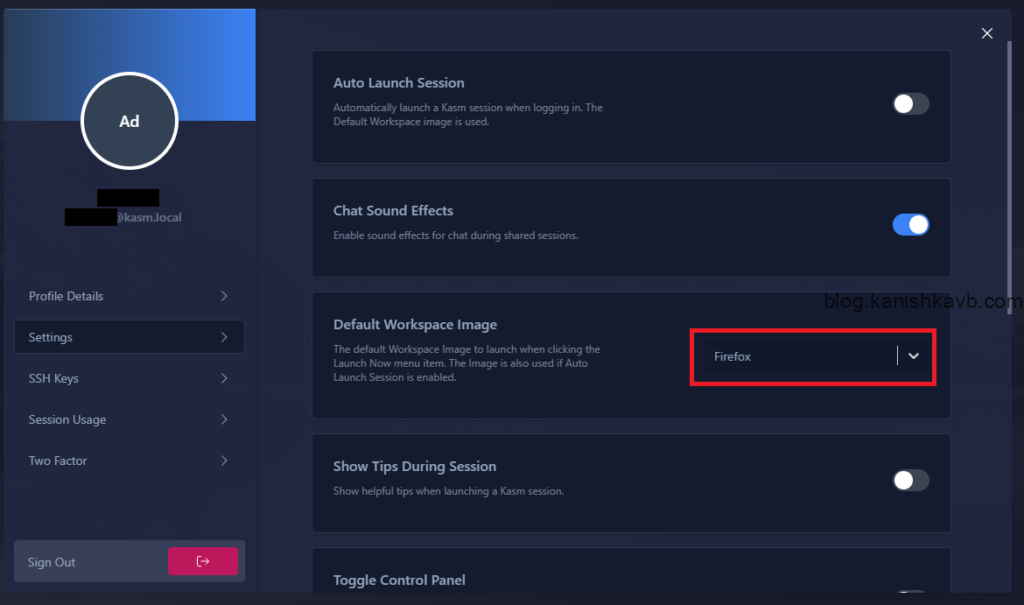
First, log into Kasm, click on your profile icon at the top right corner, go to Edit Profile. Now go to Settings and select Firefox as the Default Kasm Workspace. This is the Workspace that will be linked to the browser extension of the local machine.
Browser extension (client-side) setup
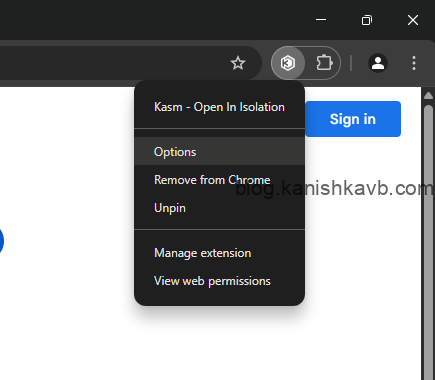
First, go to the addon/plugin store of the web browser you are using. It’s available for all major browsers. In my case I am using Google Chrome and therefore I am at Chrome web store. Now search for “Kasm – Open in Isolation” and install it.
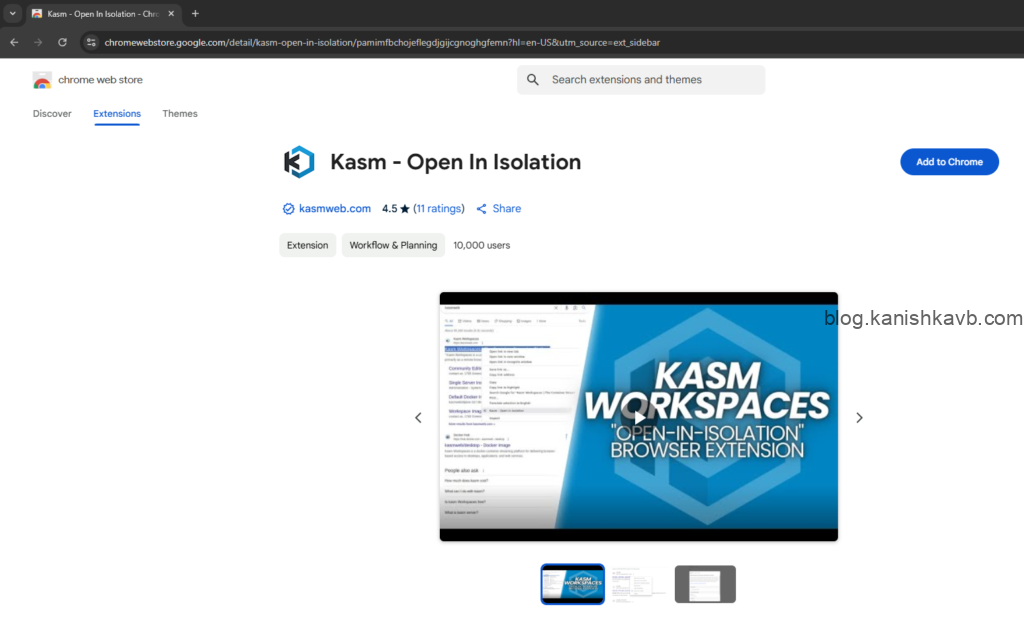
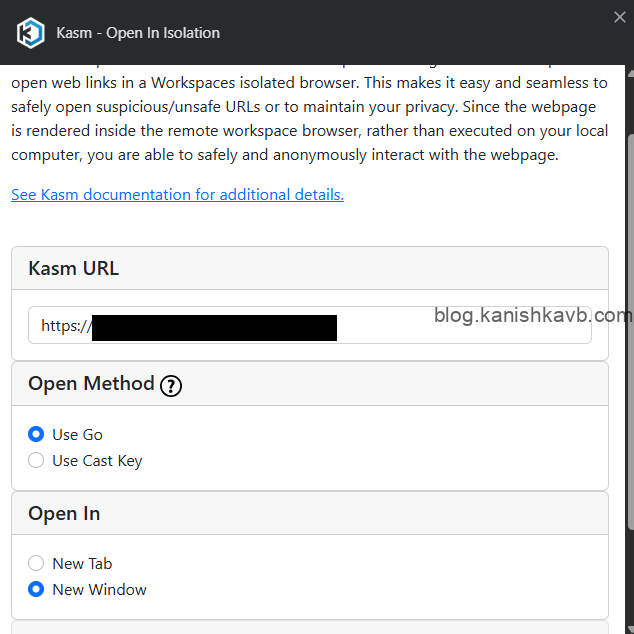
Go to options in the Kasm extension settings and add the domain/IP of your Kasm host under Kasm URL. Select whether you want the link to be opened as a new tab or a seperate window under Open in. Scroll down and save the changes.
Now Google something and right click on one of the links. Click on Open Link in Kasm option. Now, Kasm will spin up a Firefox Workspace and open the link inside it. The first time you use this feature, Kasm will ask for your login credentials. Once entered, it will remember them, and future sessions will launch automatically without needing to log in again.
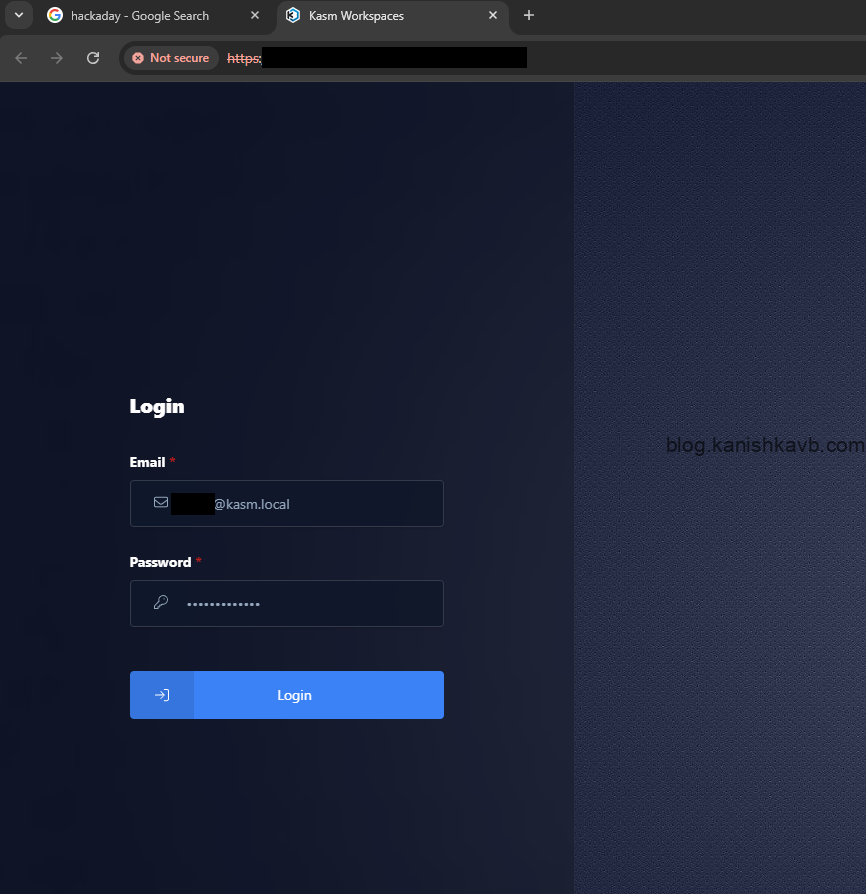
And there you have it! Just remember to destroy the session after you’re done to wipe all data and ensure a fresh start next time.
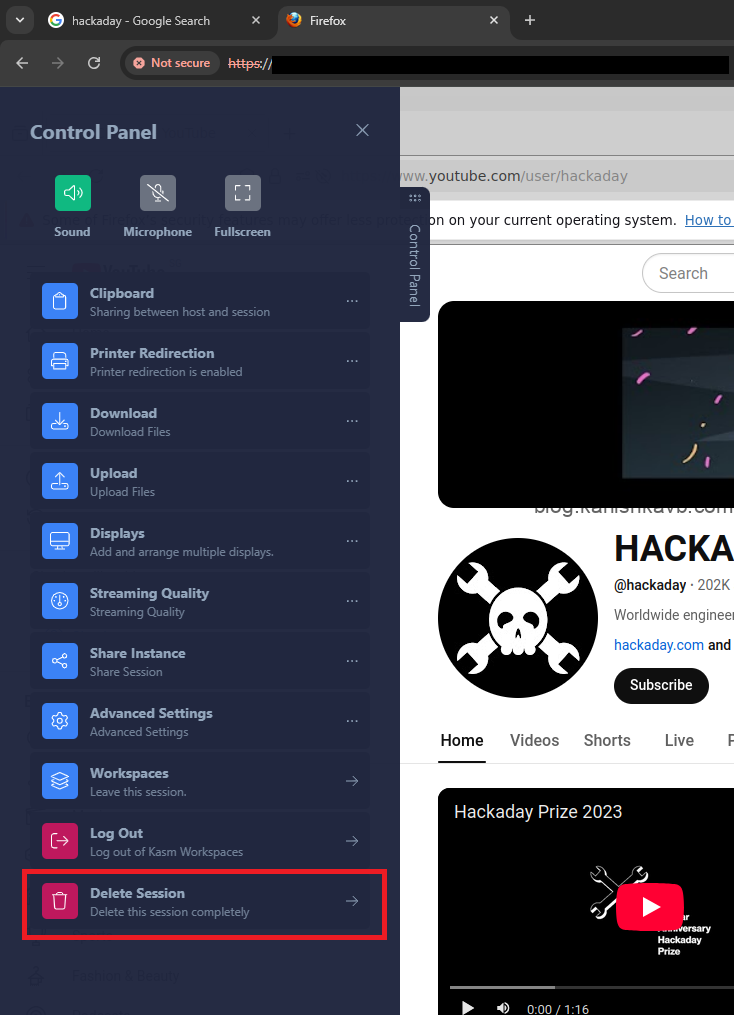
What not to do
Now that everything is set up, you might be tempted to test every link you’d usually avoid. But before you do, please keep the following in mind. This is a highly secure setup, but there are still a few things you shouldn’t do and some important risks to be aware of. Read on before diving in!
- Do not log into or use any of your real accounts within the Firefox Workspace – The security of this setup relies on the fact that the Firefox browser in the Workspace has no personal data to be exploited. The moment you log into a real, non-test account, you expose yourself to risks like cross-site scripting, fingerprinting, and cookie hijacking. Keep it isolated—no personal logins!
- Do not type any sensitive information within the Firefox Workspace – Even using incognito mode, do not type any sensitive information. Assume everything you type is captured by a keylogger, because it might as well could be if you visit the wrong site and something infects the Workspace.
- Do not store/upload any sensitive information onto the Firefox Workspace – If malware somehow escapes the browser and gains access to the Workspace, it could compromise any files stored inside.
In addition to those, using a least-privileged dedicated Kasm user for the browser extension setup would further extend the security of this platform.
Caveats
As with all things in tech, nothing is 100% secure. In my opinion, it can never be. Because security is always a balance between accessibility and restrictions. As long as your system is accessible, it cannot be 100% secure and if your system is 100% secure, it will not be accessible.
The same applies to this setup. If you’re testing or demonstrating highly volatile or irreversible actions, be aware of potential security risks.
While your local machine and the Docker container (Workspace) are completely separate, their security is only as strong as Kasm itself. If Kasm has a vulnerability, it could, in theory, be exploited. The idea of something jumping from Firefox Workspace → Kasm host → local browser → local machine is an extremely unlikely worst-case scenario, but in security, even rare threats should be acknowledged.
To minimize risks, keep Kasm and its underlying OS updated, along with your local machine and disable file uploads/downloads and clipboard access in Kasm unless absolutely necessary.
That’s it! Hope you found this helpful.
As a little teaser for the next Kasm-related post—I’m working on a guide on how to implement sidecar containers in Kasm to route traffic through a VPN. Stay tuned!

[…] Second post – How to use a Firefox Workspace as a sandboxed environment for safely opening suspicious links. […]